TRON Ecosystem Faces Potential Private Key Vulnerability
An incident occurred in the TRON ecosystem. At first glance, it appears to be a targeted hack. However, a closer look reveals a pattern that points to a potential issue in private key generation methods. This could be due to incorrect operation of the Elliptic/EC library or insufficient entropy in the runtime environment. In which case, the vulnerability would affect broad sectors of the blockchain industry. We are publishing this material to alert the community and promptly address potential security holes.
Description of the incident
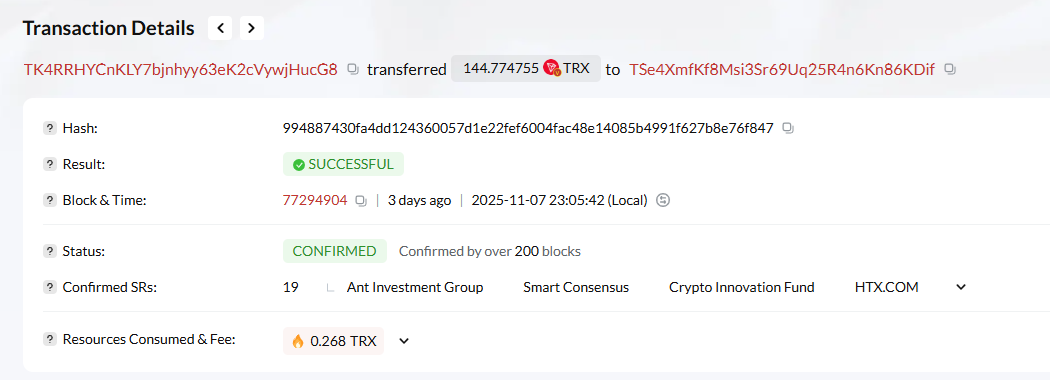
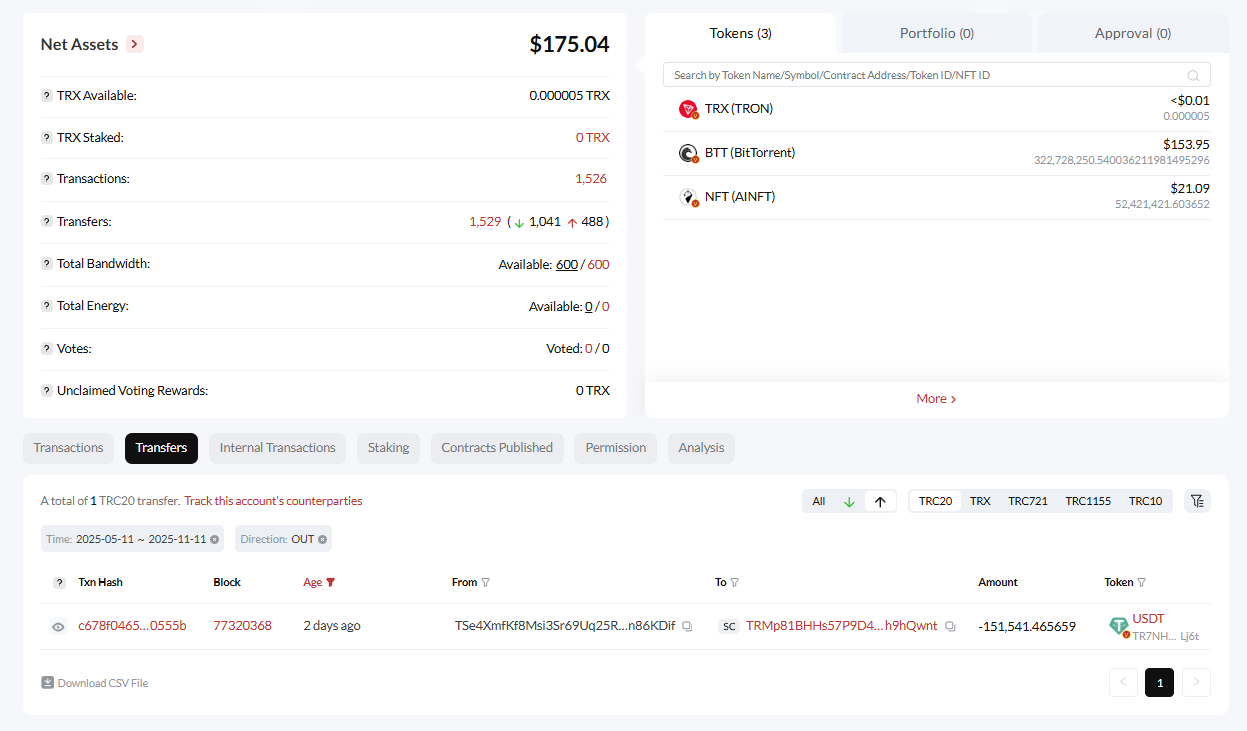
The trigger was an unexpected withdrawal of USDT from several wallets. An example of an affected wallet is TK4RRHYCnKLY7bjnhyy63eK2cVywjHucG8.
1. Withdrawal transaction. This transaction was not initiated by the wallet owner.
2. A more important transaction that occurred ~30 minutes before the withdrawal. In this transactions, the wallet granted another address the right to unlimited access to USDT:
Approve Unlimited USDT:
From: TK4RRHYCnKLY7bjnhyy63eK2cVywjHucG8
To: TSe4XmfKf8Msi3Sr69Uq25R4n6Kn86KDif
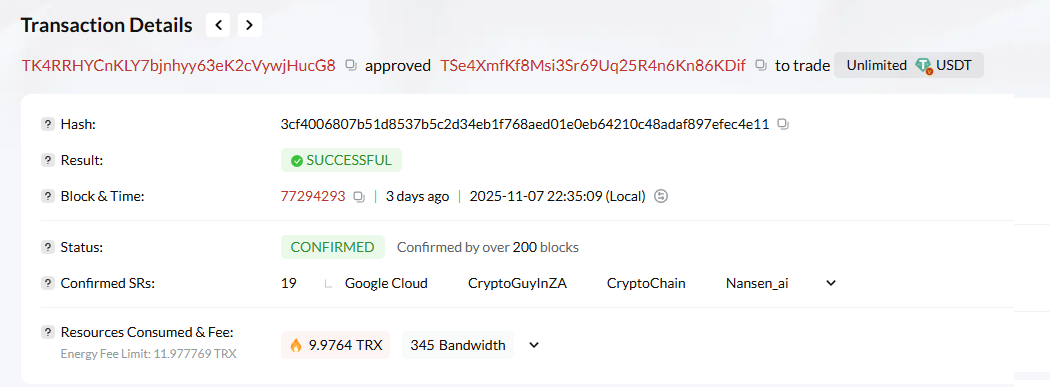
This means the attacker gained unlimited access to the USDT in the wallet without any confirmation from the owner or a system transaction. Only someone with the private key can perform such an action.
We've provided examples of two compromised wallets. However, our investigation has shown that there are thousands of such wallets.
At first, one part suffered. After some time, the other part began to be transferred.
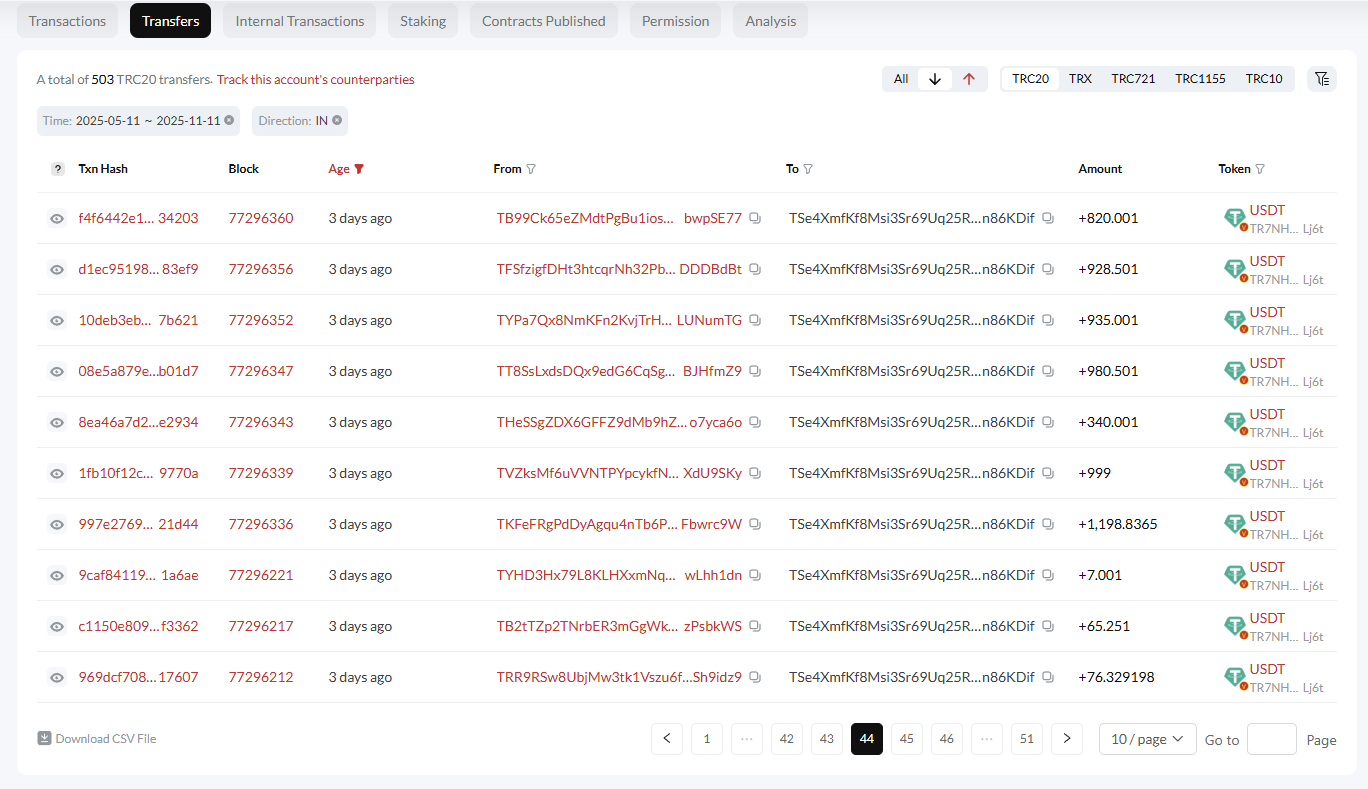
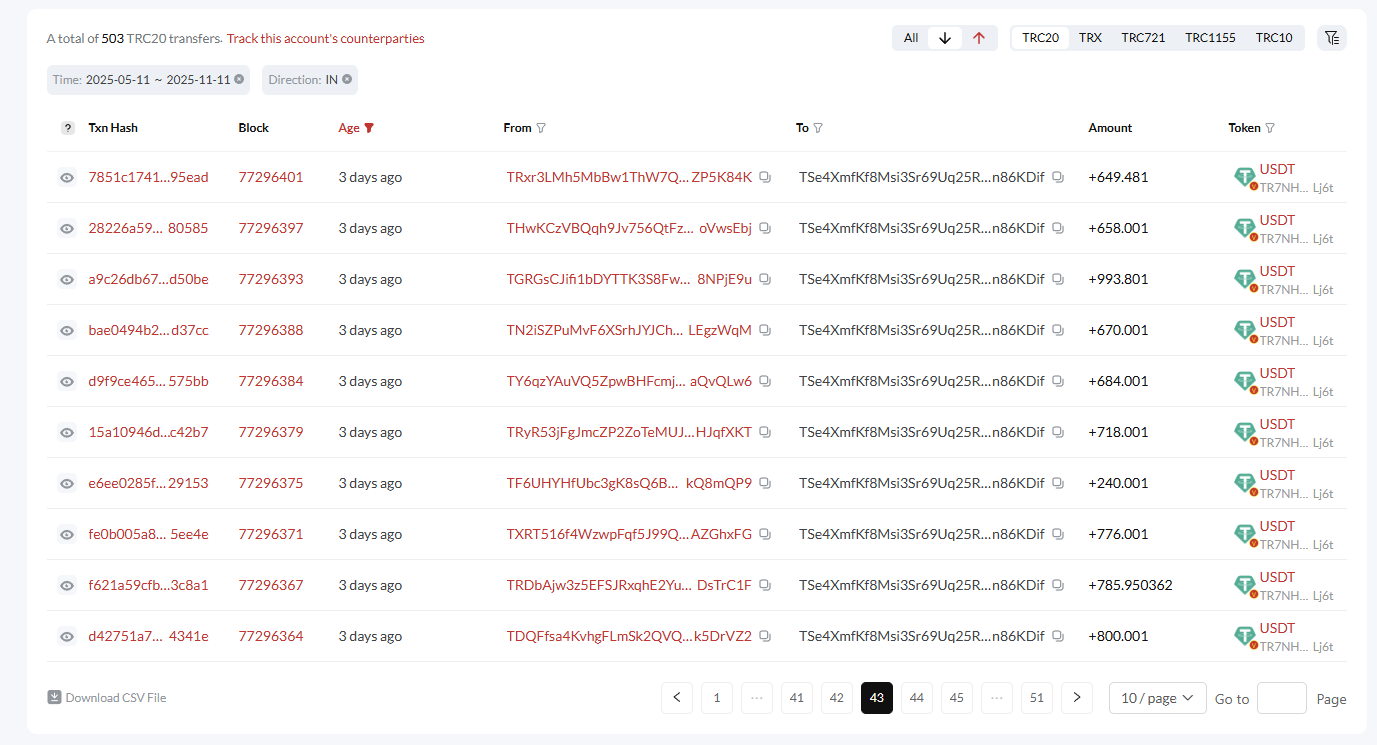
Key hypothesis
The specific method used to generate TRON wallet private keys may not have guaranteed sufficient cryptographic security. This could have led to predictability or brute-force attacks.
The wallets were likely compromised due to weak security during their creation. In this case, it can be assumed that all addresses that are currently losing USDT and TRX funds were generated without proper seed phrase generation, but rather by a specific some Elliptic/EC-based custodial solution.
This issue may affect:
- Applications that previously generated keys directly from weak entropy sources;
- Wallets created without seed phrases;
- Early versions of libraries for working with TRON accounts.
Addresses to which funds are sent
There are only two of them:
- https://tronscan.org/#/address/TSe4XmfKf8Msi3Sr69Uq25R4n6Kn86KDif
- https://tronscan.org/#/address/TTouPrmjX3nzUiy8PHGyL21J6pmiVkG8u8
From these addresses, funds are actively distributed further. The money laundering scheme is automated. The funds are sent to the HTX exchange.
Why is it important to raise the issue now?
The fact of the repeatability of the scenario and the presence of a common feature of wallet generation suggests that:
- There may be a vulnerable layer in the ecosystem, affecting the security of users' real funds.
- There is a possibility that millions of TRON users could be at risk without even knowing it.
We now recommend checking your wallets and transferring assets to new TRON accounts.
Conclusion
The incident demonstrated that threats can remain undetected and accumulate over years, especially when it comes to wallets created several years ago. We strongly recommend checking your wallets and transferring assets to newly generated TRON wallets.
